Difference between revisions of "Ophcrack"
From ERPXE Wiki
(Created page with "{{Plugin | logo = | website = http://ophcrack.sourceforge.net/ | wikipedia = http://en.wikipedia.org/wiki/Ophcrack | license = [http://en.wikipedia.org/wiki/Proprietary_software...") |
|||
| Line 42: | Line 42: | ||
}} | }} | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
[[Category:Plugins]] | [[Category:Plugins]] | ||
[[Category:Plugins-Security]] | [[Category:Plugins-Security]] | ||
Revision as of 09:56, 8 February 2012
Important information
This plugin requires a static IP address (Default is 10.0.0.1). Every change to the server IP MUST be reflected into the plugin's menu file. How to adjust ERPXE to local IP address
return to Plugins list
| Ophcrack 2.3.1 http://ophcrack.sourceforge.net/ |
|---|
Contents
Information
ERPXE Module
- Name: - Ophcrack
- Version: 2.3.1
- Official website: http://ophcrack.sourceforge.net/
- License: Proprietary software
- Wikpedia Page: http://en.wikipedia.org/wiki/Ophcrack
- Download: http://www.erpxe.com/downloads
Plugin type
| Ophcrack | Anti-Virus | Deployment | Diagnostics | OS Installation | Live Media | Recovery Tools |
|---|---|---|---|---|---|---|
| Yes | No | No | No | Yes | No |
Plugin Requirments
| Ophcrack | CIFS | HTTP | Internet | NFS | Linux OS | Windows OS |
|---|---|---|---|---|---|---|
| No | No | No | Yes | Yes | Yes |
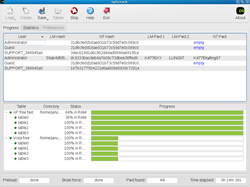
Screen Shots
Special Information
Ophcrack is a free open source (GPL licensed) program that cracks Windows passwords by using LM hashes through rainbow tables.
The program includes the ability to import the hashes from a variety of formats, including dumping directly from the SAM files of Windows.
On most computers, ophcrack can crack most passwords within a few minutes.
Linux Installation Instructions
Download ophcrack231-XXX.tar.gz to /
https://sourceforge.net/projects/erpxe/files/plugins/
extract ophcrack231-XXX.tar.gz file:
tar -xvzf ophcrack231-XXX.tar.gz
Download ophcrack 2.3.1 ISO Latest Version to /mnt/ :
http://research.pandasecurity.com/technology/1004/
Mount ISO file to temporary location (/mnt/cdrom/)
mkdir /mnt/cdrom/ mount -o loop /mnt/SafeCD.iso /mnt/cdrom/